As cyber-attacks are increasing day by day, Internet users are becoming more concerned while downloading applications from the Internet. Automated software is automatically assimilated by standard security solutions, as a threat from an unknown source. How can developers avoid this situation and thus increase the number of downloads of their applications?
What is a code signing certificate and why it is required to sign a code?
Code signing is a digital certificate which contains some information through which an individual or organization can be identified. It has been generated by the certification authority. In this certificate the developers can include information about themselves in their applications or programs, as well as create a digital signature (sign code).
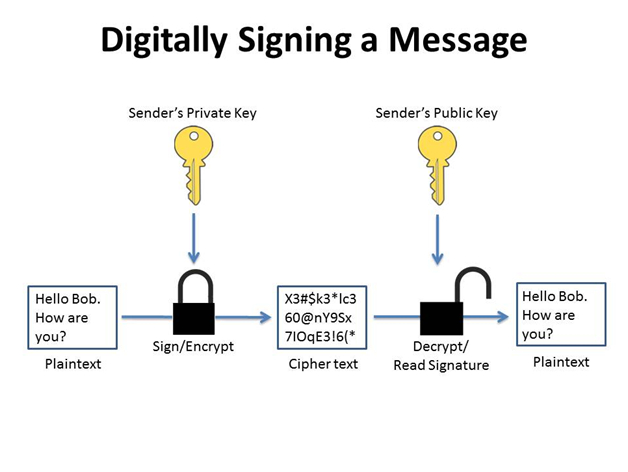
It is a digital certificate that binds an organization to a public key, which itself is connected with a corresponding private key. The private key is used to implement a digital signature in a smaller version of the code executed through a hash algorithm and the public key to validate the signature.
By signing a hash of a code, it becomes easy to discover that after a signature whether any changes are accured or not. Converting any character to a line of code changes the hash, raising suspicion.
Code signature in practice
Code signing certificates, enables developers to digitally sign unlimited number of applications that they will then distribute over the Internet, as well as affix them a time stamp to prevent signature expiration. This digital signature process is the virtual equivalent of plastic wrapping for programs distributed in CD form.
Therefore, by signing a code developer ensure their users that their program is valid, consistent with the initial development, and that the code has been entered between its creation and its publication and no changes have been made.
Code signature certificates guarantee the authenticity, security and integrity of a signed program, and thus will bring an additional level of trust to the installation process, greatly reducing the number of program download abandonments.
How code signing works?
Code signing is realized using public key encryption technology incorporated with a hash algorithm. The software developer generates a private key (.pvk) and certificate request file (CSR) on its computer and introduced it to the CA organization. The CA organization authenticates the correct identity of the software developer according to international standards. Issue a code signing certificate.
Software developers use code signing tools to generate a hash value for the code, a private key to encrypt the hash value to generate a signature summary, and a public key (certificate), signature summary and software package. Code network in order to generate a signed software code, publish the signed code on the network.
When downloading, the end user can authenticate the validity and legitimacy of the public key (certificate) with the help of the system’s trusted root certificate list in order to confirm that the code comes from a genuine and trusted software developer.
The public key decreases the hash value in the signature; compare the digested and newly generated hash values, and the hash digest is consistent, hinting that the software code has not been tampered with during the transmission process, confirming code integration.

